Other Attacks using Delorean
Have a look to other posts of this serie:
[7] Other Attacks
[8] Helper tools
Disclaimer: All this information has been obtained from empirical tests and in a specific period of time, so they could have changed.
[7] Other Attacks
[8] Helper tools
Disclaimer: All this information has been obtained from empirical tests and in a specific period of time, so they could have changed.
The attacks shown in the previous posts are the ones that I considered more likely and with biggest impact. However, I was trying other exploitation opportunities using time synchronization attacks. Some of them worked even being unlikely, and some others didn't work at all.
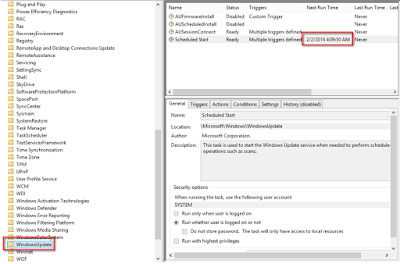
One of the attacks that worked was an attack against the Windows Task Scheduler. As you probably know, there is a service in Windows boxes that run certain maintenance tasks in the background, such as the same time synchronization.
The task scheduler keeps information about the last time when the task was ran and the next time it will do. These fields are important because, depending on the task configuration, "Next Run Time" is sometimes calculated based on the "Last Run time", which gives us the opportunity to manipulate the next run time by manipulating the clock using Delorean.
As I said, not all the tasks calculate "Next Run Time" in this way, but there are some interesting tasks that do, for example the Windows Automatic Updated Service.
So, What happen if we manipulate the the clock using Delorean, as we did in previous posts, and the Windows Automatic Update task is executed? The "Last Run Time" field would be updated to the fake date (let's said 2020), so the "Next Run Time" would be calculated in base of that date, in other words, at some point in 2020. That should't be a problem if the system would maintain that fake date forever, but if the clock is restored to the real date... then the next Windows Automatic Update will take place in 4 years, so the users wouldn't be warned about new updates and fixes if they don't manually check it.
This is an unlikely attack because Windows is the mosts unlikely platform to be a victim for a Delorean attack, and because I couldn't find a way to restore the clock without user intervention. However, other tasks and other platforms (cron in Linux, for example) could be abused in the same way.
Written on January 25, 2016